[ad_1]
Just one of the main challenges in the databases globe is SQL injection – it is prevalent to such an extent that even OWASP constantly lists it as the #1 risk targeting net purposes. SQL injection can have many forms, and a person of these types is blind SQL injection – in this web site post, we will go via just how hazardous this sort of an assault can be.
What Is SQL Injection? What Are Its Groups?
SQL injection is the major assault directed at databases – an software is vulnerable to SQL injection when an enter delivered by a consumer is forwarded straight into a database with out becoming sanitized and appropriately dealt with.
The categories of SQL injection are extremely essential to comprehend simply because of a few of vital good reasons:
- Different sorts of SQL injection impact internet programs in distinctive methods.
- Some varieties of SQL injection can be more quickly prevented than other people.
- Some sorts of SQL injection depend straight on the attributes of our net applications (e.g., the results of a thriving blind SQL injection attack are directly dependent on regardless of whether our internet software is exhibiting mistakes or not.)
- Some kinds of SQL injection assaults have sub-varieties (imagine time-based mostly blind SQL injection) – these sub-types could possibly make or crack a deal for a nefarious occasion as very well simply because they are specifically dependent on a particular variable that, in this circumstance, can not be controlled, and so they are direct – time.
SQL injection has a couple of groups:
|
SQL Injection Classification |
About |
|
Vintage SQL injection |
The most prevalent SQL injection form. These kinds of an injection kind is most commonly detected (and most famously depicted by script kiddies as being “very basic to use”) by including a one-quote sign to a GET parameter that is then evaluated by a databases. |
|
Out-of-band SQL injection |
Such a form of SQL injection that can be detected making use of OOB (out-of-band) approaches – features that could help detect these types of a form of injection include |
|
Blind SQL injection |
These a sort of SQL injection wherever an software does not return any glitches – as these kinds of, an attacker is not in a position to ascertain irrespective of whether his or her destructive question was correctly executed or not: in these types of a scenario, the benefits of a query are frequently made a decision by hunting at the webpage that is currently being attacked itself – a blank website page that is currently being returned almost certainly has no effects though if an attacker submits a malformed question, it ought to return the very same website page (that could probably look a minimal odd given that some issues may possibly be lacking, and so on.) |
As you can see, there are not that lots of types SQL injection falls underneath – nevertheless, even though common SQL injection is becoming made use of the most commonly when basic SQL injection assaults do not do the job, attackers typically switch to the blind side of SQL – they consider attacking applications with blind SQL injection.
The Kingdom of Blind SQL Injection
Assume of your software as a castle. We know this could possibly appear at minimum a very little bit odd but bear with us. Now, visualize your website application as a castle. Performed? Alright, consider that a bunch of blind soldiers with spears are attacking it and their spears regularly overlook the fortified defenses of the castle. What do you think – how a great deal time do the blind soldiers with spears have to spare to be done with your castle’s defenses? It will choose a though, but the soldiers will ultimately get through. That is correct – and after the soldiers get as a result of, the treasures you retail outlet in your castle (the info inside of your world wide web applications) are cactus – they will steal all the things.
Soldiers are effectively-geared up, and even although they are blind, they will inevitably perpetrate your defenses – oh, noes! That’s fairly substantially how blind SQL injection works in the true planet, so let us give you another instance:
- An attacker finds your world wide web application to be vulnerable to a blind sort of SQL injection by including a solitary estimate just after a particular parameter – then your net application returns an error.
- An attacker keeps crafting SQL queries – none of them return any error. Having said that, he speedily finds that if he executes one sort of query, the info inside of your net application demonstrates on the display screen, just after he executes another – the details disappears. “Aha!”, – thinks the attacker. “Gotcha. Received a blind SQL injection flaw.”
As you may presently recognize, a blind SQL injection is an attack that asks the database “inquiries” in a kind of queries and attempts to establish no matter whether they are correct or phony centered on the response on the world wide web software. Blind SQL injection is most routinely detected by managing queries like so:
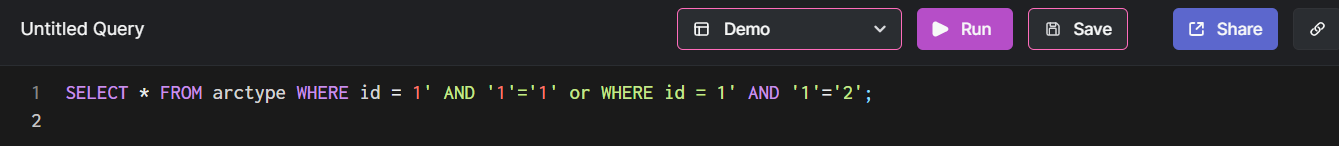
If a world wide web application returns a “constructive” response (that means that it returns a noticeable variance on a world-wide-web web page), the world-wide-web software is vulnerable to such an attack, although if an application is indifferent, it is possibly not. In the 1st state of affairs, the attacker will know something’s up with your database and try out to penetrate your defenses even more. And so the recreation commences – the attacker is striving to notice what kind of responses your net software is eager to return. A question returns a web page with outcomes – Okay, they probe further more, a question returns a blank page – hmmm… they improve the question and check out again. And so the recreation proceeds till all details that interests a nefarious bash is extracted from your database. Sure, these kinds of sort of querying will get a lengthy time (and that’s one of the issues blind SQL injection is mainly known for), but retain in thoughts that time, as sad as it could possibly be, possibly will not halt an attacker that has an purpose to damage your techniques as a lot as possible or steal all of your information.
Some net apps might even filter the sections in GET or Publish parameters meaning that they may well “catch” solitary or double rates getting used, but which is only one particular piece of the puzzle. Such a perform is commonly a section of a world-wide-web software firewall form of performance – we have by now mentioned WAFs (shorter for Web Software Firewalls) in one more posting of ours, so we is not going to go as well significantly into depth, but hold in head that internet application firewalls deflect all varieties of attacks ranging from Denial of Company to, you guessed it, SQL injection.
Varieties of Blind SQL Injection
There are two kinds of blind SQL injection – boolean-dependent and time-dependent. Boolean-based blind SQL injection is reliant on sending a specified SQL query to the databases to identify whether or not the question returns a Real or Wrong result by hunting at the response of the software, though time-based mostly SQL injection is reliant on time – a query probing a website application for blind time-centered SQL injection will force the databases to hold out a few of seconds right before returning a response, and if the reaction is returned right after the precise quantity of specified seconds has handed, the attacker will be able to determine that the application is prone to blind, time-based SQL injection. Listed here are a pair of essential distinctions and similarities between the two kinds:
| Style of Blind SQL Injection | Vital Facet |
|---|---|
| Time-based mostly | Reliant on the response of the world-wide-web software |
| Boolean-dependent | Reliant on the reaction of the net software |
| Time-centered | Reliant on time |
| Boolean-based mostly | Reliant on the “physical appearance” of the world wide web software |
| Time-centered | Normally gradual simply because of the time expected to verify whether or not each and every question that was run executed effectively |
| Boolean-based mostly | Normally sluggish mainly because of the time put in analyzing the responses of the software in a visual method |
| Time-dependent and Boolean-centered | Generally prevented by utilizing basic security steps this sort of as organized statements, input validation, enforcing the theory of minimum privilege, etc. |
Safeguarding From Blind SQL Injection
Safeguarding from a blind variety of SQL injection, opposite to well-liked perception, does not consider considerably talent or work – it can be prevented applying simple security measures. Sure, it is as uncomplicated as that! We can attain that by applying Ready Info Objects (PDO) in PHP (they break up the enter furnished by the user and the relaxation of the query, so any sort of SQL injection is not attainable) by working with automated screening solutions that advise us irrespective of whether or not our application is susceptible to SQLi, or, of program, making use of whitelist protection controls – we, as builders, should really have a habit of filtering and sanitizing every single sort of parameter that somehow interacts with our info. By executing that , we can place our net purposes at the upcoming safety stage each by preserving in opposition to all varieties of SQL injection assaults and other types of security issues.
Once we place our world wide web purposes at the next amount of safety, we ought to take treatment of the stability of our individual accounts much too – we can run a search by means of BreachDirectory to see if any of our accounts are at possibility and act according to the information supplied to us. At the time we do that, our accounts need to be safe as properly. Win-win!
Blind SQL injection is a form of SQL injection in which an attacker can not determine out how our net purposes “think”, so as a substitute, he or she has to rely on the output a web application provides us or depend on time, relying on which method (boolean-dependent or time-based mostly) is in use. When relying on boolean-centered SQL injection, an attacker counts on the point that the world wide web software could possibly seem various than usual, whilst when applying time-primarily based SQL injection, the attacker heavily depends on time.
No subject what sort of SQL injection is elected to use by the attacker, no form delivers the attacker with a speedy way to get facts – an attacker may perhaps literally spend hrs, times, or even months attaining details of curiosity to him, but at the time the attack is productively completed, it will normally be bought on the darkish web for hundreds of dollars to other nefarious get-togethers, and the cycle will continue on.
To guard towards blind SQL injection, make sure to utilize safe coding procedures, do not ahead user enter straight into a database, and refine how glitches are returned in your world-wide-web apps.
Moreover, make positive to run a look for as a result of known information breach search engines to ensure that your info is secure both equally through the day and the night time and until the next time. See you in the next web site!
[ad_2]